
DISCLAIMER: Just to be clear, this article is not to dissuade people from using dating apps. We are simply calling for users to pay attention to their physical safety and privacy while using these applications.
Introduction To Dating Apps
Ah yes, dating apps. Millennials and Gen-Z are addicted to them for their "no-strings-attached" fun. Romantic moralists hate them for their emphasis on looks rather than personality. Not everyone is a fan of these apps, but Tinder, Grindr, Bumble, Hinge, and more apps have become the staple method for users to find love and get lucky.
Especially during the COVID-19 pandemic –where many of the world's singles were isolated in lockdown- dating apps became the essential tool to talk to new people rather than your cat. According to fortune.com, the number of dates on OkCupid increased a shocking 700% during the first few months of the pandemic, in addition to Bumble's 70% increase in the number of video calls performed by users.
For many people, using technology to find love has never been easier, so what's not to like? Well, there is one group of "tin-foil hat pessimists" who hate dating apps with a passion and want to see them die. You can call us love-hating cynics, but we cyber professionals have a lot of good reasons to put these apps to shame. However, we just want to make sure that users are being protected, physically and on a digital scale. Therefore, it's time that we gave a full review: Which dating app is the safest to use?
Experiment Rundown
The Apps In Question:
For this study, we decided to review the "Big Three" dating apps: Tinder, Hinge, and Bumble, due to their common use by users and the amount of information available for each app. While there are several other dating apps on the market, it seems like these three gain the most attention and frequent participation.
Resources:
Most of the information obtained about each dating app was gathered from public records available online (Privacy Policies, Company Websites, Company Blog posts, etc.). We also went through the process of creating individual user accounts to get an idea of how much information each app collected about users and what privacy settings were available for each account.
Security Categories:
We established four comprehensive categories to measure each dating app's cybersecurity practices:
1. Application/Infrastructure Security
This category focused specifically on each application’s dating algorithm and its associated security features (end-to-end encryption, tunneling, authentication methods, zero-day exploits, etc.).
2. Monitoring & Threat Management
This category looks at how well each app monitors the environment for common cybersecurity threats targeting dating app users (identity theft, phishing attacks, social engineering schemes, etc.). We also measured each app’s ability to respond to incidents in real-time based on past case-scenarios, and whether companies did well to identify emerging threats and trends in the cybersecurity industry.
3. Governance & Compliance
This category considers each app’s compliance with national and international data privacy laws such as the General Data Protection Regulation and individual state privacy laws. We also reviewed company policies and individual user policies that help safeguard a user’s digital media and identity.
4. User Privacy & Physical Safety
This category considers factors such as how much confidential data is being collected on an on-going basis from the user, how many parties have access to user information, and physical safety features (panic buttons, 24/7 emergency response, etc.) Clarification: Our take on "essential data" means any data that is essential to a user building a public profile on the app that does not compromise all of the details of their private life, but reveals just enough to result in the success of their matching algorithm. For example: When searching for individuals that strike your fancy, you may want to know their name, age, or sexual orientation along with hobbies and other nice details about their life. Data that would be irrelevant in finding matches would include their credit card number or social security number (yikes, hopefully it's not that bad).
Essential Data | Non-Essential Data |
-Name | -Financial info. (credit cards, how much a user's salary is, etc.) |
-Gender | -Race/ethnicity, household type, family relationships (other population demographics) |
-Age | -Real time status activity updates on a user's location (broadcasted to the public) |
-Sexual Orientation | -Other personally identifiable information (PII) such as social security numbers, usernames, email addresses, phone numbers, etc. (broadcasted to the public) |
Security Scale:
To measure each app's security, we chose a 1-3 ranking scale for each category (1 being worst security and 3 being the best). At the end, we totaled up each app's score out of 10. Whichever app scored the highest was deemed the most secure to use. An example scale is shown below:
| Application/Infrastructure Security | Monitoring & Threat Management | Governance & Compliance | User Privacy & Safety |
1 | Little to no encryption, no use of VPN, no authentication methods required, history of numerous security vulnerabilities | Pays little to no attention to emerging cybersecurity threats, history of poor incident response strategy | Complies with very few state data privacy laws and generally does not comply with the GDPR, poorly detailed user or company policies | Very few or no physical safety measures installed for users, multiple parties have access to confidential data, user data remains virtually unprotected |
2 | There is some encryption utilized by the app but there could be more. One or more authentication methods are required, there have been some security vulnerabilities. | Identifies some cybersecurity threats and provides basic incident response procedures in event of a cyber attack | Complies with most of the GDPR and most state privacy laws. User and company privacy policies are widely available and have some useful insight | There are some physical safety measures available in the app, only a few parties have access to confidential user data, and there is basic protection for user data |
3 | There is encryption employed through most or all of the app's functions and multiple authentication methods are required. Little to no security vulnerabilities. | Identifies and openly acknowledges several cybersecurity threats and provides intelligent incident response tactics. | Complies with all standards established in the GDPR and all state laws. There are also several detailed user and company privacy policies available to the public. | There are several physical safety features available for users when they should need help. The app only collects data essential to the app and respects user privacy. |
Security Review #1: Tinder
There were actually some surprising finds about Tinder's company security practices, meaning some of them were not as bad as expected. Here is how Tinder scored in each category:
Application/Infrastructure Security | Monitoring & Threat Management | Governance & Compliance | User Privacy & Safety |
2 | 2 | 1 | 1.5 |
OVERALL SCORE = 6.5 / 10 (Could be better)
Application/Infrastructure Security:
Positives: Tinder employs Two-Factor Authentication, SSL encryption for the app's messaging mechanism, and all online traffic is HTTPS encrypted.
Negatives: We were surprised to find no end-to-end encryption to protect a user's images, messaging, and overall profile information. There were also three major security vulnerabilities that the company suffered in the past 5 years, found on the NIST CVE database website. Read about them here.
Monitoring & Threat Management:
Positives: It's surprising to see, but Tinder actually pays pretty good attention to emerging cybersecurity threats and vulnerabilities. From what we could find, the company employs continuous security assessments, security design reviews, penetration testing, and vulnerability scanning performed by a dedicated Red Team. They also have an ongoing Bug Bounty competition that is open to the public for discovering zero-day vulnerabilities, which is a sign that they stay up-to-date on latest cyber trends.
Negatives: In past cyber attacks, we found cases of Tinder performing strategic incident response. According to a cybersecurity-insider article about a major cat-fishing scandal, Tinder was reportedly quick to remove data from compromised servers and took full responsibility for the attack. Whether they applied the lessons learned, only that can be discovered from inside the company. However, for this category, we definitely liked what we saw.
Governance & Compliance

Positives: Tinder published on their website that they are the first dating app to be recognized for their information security management program, which is fantastic. They are also ISO/IEC 27001 certified, which means that they follow international standards for information security management.
Negatives: It's no secret that Tinder regularly does whatever they want wherever they want, and it does not matter where you fall location-wise on that scale. When reviewing their Privacy Policy, there was a lot of information about who is responsible for a user's privacy depending on where they live in the world, but Tinder is not actually on that list. It's clear that they are passing off that responsibility to numerous other parties, which comes off as both confusing and irresponsible.
The system of "Privacy Request Appeals", in which if a user sends the company a request to delete their data after no longer wanting to be involved with the app, also comes off as absurd. Here at Siliconaiandcyber.com, we just really wish that was not a thing and that as soon as users want out of a tech agreement, the company just obliges. But nope! Tinder has a long and detailed clause in their Privacy Policy stating that they can use your data "as long as they need it". If you close your account and expect data to be deleted, it may not be if it supports their "legitimate business purposes". Therefore, take this as a warning: If you sign up for Tinder and later want your data back, be prepared to fight for it. Among numerous other instances where Tinder did not respect the GDPR or other state privacy laws, we had to score this category at the lowest.
User Privacy & Safety:
Positives: This category was a tough one to decide on because while Tinder has excellent physical safety features built into its app, they really don't respect user privacy that much (at least from our standards). However, if you are using the app, you can feel safe knowing that before you go on a blind date there are multiple features to protect your safety, including connection to Noonlight (an emergency response app that alerts close friends and family where you are), "Does This Bother You?" (prompts within Tinder messaging that encourage users to report suspicious activity), Tinder panic button (immediately alerts safety authorities if something goes wrong), etc.
Negatives: Looking at how many groups have access to confidential data on Tinder's website was a little daunting. The list just keeps going and going, but some of the groups on this list really don't need access to this much user data, like the "various partners" and affiliate groups that Tinder works with. As you can expect, that list turns into a complicated web of hundreds upon thousands of people that can access your data, which can be a little alarming.
While creating a dummy account on Tinder, we also went through a laborious process of information giving that would make any cyber professional squirm in discomfort. Tinder lists the following information on their privacy policy that they are entitled to receiving:
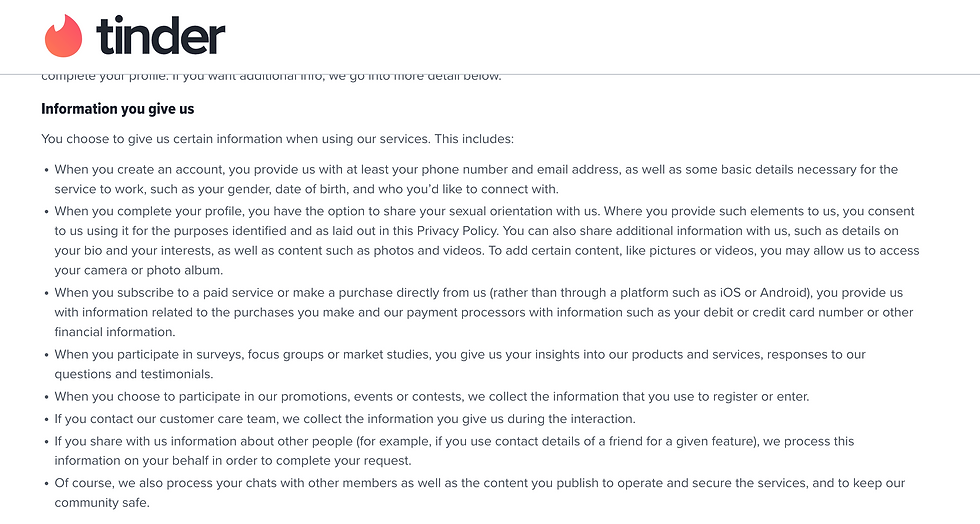
However, in the account creation process, they asked for a lot more personal information than the things listed on their website. It was a little weird that they asked whether your correspondent wanted to import all details from their Instagram, Facebook, and Apple accounts (about 800 pages of data!). There is also a lot of strategic marketing that goes into making the "perfect" Tinder profile, but just remember to be aware of what photos you are posting and the ways that people can take advantage of them. Social engineering is the most common method of attack that takes place on dating app platforms, and anyone can figure out personal details about you by looking at a photo.
Security Review #2: Bumble

After reviewing Tinder, we were so happy to find that Bumble seems to really care about their users' privacy, so great job to them! Here is how they scored in each category:
Application/Infrastructure Security | Monitoring & Threat Management | Compliance & Governance | User Privacy & Safety |
2 | 2 | 3 | 2 |
OVERALL SCORE = 9 / 10 (Pretty Good)
Application & Infrastructure Security:
Positives: According to research available online, Bumble protects their application security by encrypting all data while in-transit and encrypting their destination servers. We have to assume that they use some form of TLS/SSL, and we can only hope that they use Public Key Infrastructure (PKI) to asymmetrically secure their certificates. Bumble also enables 2-factor authentication which forces a user to prove their identity, plus they send a standard verification code that is alerted by unusual login attempts. Something that's also interesting is their use of mandatory biometrics to verify a user's physical appearance. As a result, you can expect a lesser chance of being cat-fished when using Bumble's platform.
Negatives: Like Tinder, it appears that Bumble does not enable end-to-end encryption, which was a little disappointing. Along with that, a major vulnerability was found in which Bumble was leaking users' precise geolocation status (yikes). Read about that here. For this reason, their score is similar to Tinder's when it comes to app/infrastructure security.
Monitoring & Threat Management:
Positives: Bumble appears to be very forward-thinking when it comes to monitoring current and future security threats. It was nice to see that they acknowledged the use of photo-verification as a method to counter bots and other identity/cat-fishing schemes, as well as their frequent discussions about "what we can do more" to increase user security. Bumble also performs regular security assessments, maintains a Security Operations Center (SOC) team, red team, and other well-built cybersecurity positions. They also host an ongoing bug-bounty program.
Negatives: Honestly, there aren't many negatives. Bumble is pretty active by attending cybersecurity conferences and they put in the effort to promote security awareness training to employees and their users. Even though they had some trouble with the big geolocation data breach, we would say they work hard to not repeat mistakes. However, the compromise of customers' location data is a big no-no in the security world, so we have to rank this category as a 2. Read about their security commitments here:

Compliance & Governance:
Positives: Just reading about Bumble's data compliance and governance policies was so satisfying because you can tell that they are 100% transparent. At least with what was found online, Bumble has pages upon pages of information security documentation that is open to the public; such a nice courtesy! Their Privacy Policy is very thorough in detailing exactly how much data users are giving up about themselves and what that data is being used for. They also have an entire section discussing their compliance with the GDPR and other state privacy laws. It was also wonderful to see them acknowledge and detail a user's rights to privacy, available on their website:

Data is also only stored on servers in the United States and the UK, which comes as a relief to Western users conscious of nation-state spying.
Negatives: None, so far as we can tell. If we had to choose a dating app (still don't recommend it), we would go with Bumble due to their excellent transparency and sensitivity to privacy laws.
User Privacy & Safety:
Positives: Bumble seems to care about their users' privacy and safety because they go extra lengths to ensure that users understand their data sharing rights. They also encourage their users not to disclose confidential information about themselves on the app, and access to confidential data seems limited, to an extent. Bumble also employs a few safety features, such as their robust "Block & Report" mechanism and photo verification before in-person dates.
Negatives: Hopefully Bumble employs the principle of "least privilege" when granting access to coveted user data, but not much was found concerning this topic. Since Bumble also syncs users' social media accounts with their profiles, that leaves a lot of data floating around that is probably being accessed by multiple parties.
Security Review #3: Hinge

After reviewing Hinge, it was a little tricky to determine their scores because a lot of their negatives cancelled out their positives, so lot's of highs and lows with this one. Here is how they scored in each category:
Application/Infrastructure Security | Monitoring & Threat Management | Compliance & Governance | User Privacy & Safety |
2 | 2 | 2 | 1.5 |
OVERALL SCORE = 7.5 / 10 (Could Be Better)
Application & Infrastructure Security:
Positives: Not a lot of information was found on Hinge's application/infrastructure security, but what was found is pretty good. User data is encrypted in transit and at rest while being stored on cloud servers, so we can only assume they enable TLS/SSL and HTTPS encryption over the cloud. Hinge reportedly also logs all access to their application infrastructure and associated systems, which is good! Additionally, they claim to implement security at all lifecycle stages of their app, and that is always wonderful to hear. It seems like Hinge has somewhat of a security mindset.
Negatives: Unfortunately, hinge is prone to several highly public security vulnerabilities, including cross-site scripting (XSS- type of injection attack in which malicious scripts are injected into benign websites or applications). Hinge also suffered from media access controls being exploited due to a third-party open vulnerability. Adversaries took advantage of the default configuration of the Cloudinary Image Transformation API. Read about these vulnerabilities here and here. Overall, it seems that Hinge offers better encryption than Tinder but we cannot grant it full marks in this category due to their vulnerability history.
Monitoring & Threat Management:
Positives: According to what is available in their Privacy Policy, Hinge does conduct regular security assessments both internally and from external third party auditors. Like Tinder and Bumble, they also have a highly active bug bounty program and they do employ a round-the-clock red team. It seems like the rest of Hinge's security department is pretty built out with several data privacy teams (including a Security Operations Center) to help monitor and detect threats to the app.
Negatives: That being said, they could always do more. Like Tinder and Bumble, it is unknown whether Hinge employs a SIEM like CrowdStrike to actively monitor their threat environment (that info is guarded by the company), and we have to acknowledge their ability to handle security vulnerabilities like the ones previously discussed. There is little information available about Hinge's incident response strategies, so we can only hope that they actually have some.
Compliance & Governance:
Positives: When it comes to compliance, Hinge does acknowledge their obedience to the GDPR and individual state laws (especially California and the CCPA). It was also very nice of them to post their information security mission statement for anyone to view on their website (which every organization should do). This just shows that they are verbally committed to transparency and seem to care about their users' privacy rights. They are also very transparent as to who is responsible for your data depending on whether you live within or outside of the EU, and unlike Tinder, Hinge takes most of the responsibility. We also loved their transparency provided for a user's individual data privacy rights, shown below:


Negatives: There are not many negatives for Hinge in this category other than the lack of transparency for cross-border data transfers. This is also a slight problem for all other dating apps and services, but we thought that Hinge could be a little less vague on that concept. Overall, Hinge is a little less thorough than Bumble but still provides pretty good transparency.
User Privacy & Safety:
Positives: This was a tough category to rank. We loved the "First Date Check-In" feature, which requires a user to submit honest feedback about how the date is going in real time. Hinge also employs several robust reporting features which allows a user to report any suspicious activity at any stage of their dating experience. These reporting tools are monitored with Machine Learning and human safety experts who decide the next best steps to take in the event of a safety emergency. Along with physical safety, Hinge proved to break down Data Usage and Shared Parties very thoroughly on their website. Not only did they list all user privacy rights, but they also restrict access to user data by employing least privilege among employees (fabulous!). Hinge also requires all users to provide proof of identity in order to access their data, and they seem to hold few qualms about a user wanting to delete their account/associated content.
Negatives: Hinge has a lot of positives referring to user privacy and safety, but they could always do more. They could learn something from Tinder by employing more physical safety features within the app, but instead they only advise "dating safety tips" on their website. When it comes to syncing social media accounts with the app, Instagram is regularly updated with a user's activity in affiliation to their usage of Hinge, which is not great. Hinge is also part of the MatchGroup.com family of businesses, meaning that the data they share with third-party vendors probably includes a highly-complex web of people, so your data is actually being accessed by a lot of parties. Therefore, Hinge unfortunately earned a 1.5 due to the number of negatives cancelling out their positives.
Conclusion: What Did We Learn Here?

At the conclusion of this experiment, the question should be more about "what did we not learn?" It's no secret that dating apps collect a heck ton of information from a user (about 800 pages worth), so it is probably better for your personal cybersecurity if you did not use them at all. However, at silicon, a winner must be declared, so if you have to use a dating app, Bumble would probably be the best choice (congratulations to them). However, hopefully this study did reveal some concerns about the dating app business, and we can clearly point out three major ones:
CONCERN #1: Dating Apps Can Be Dangerous
After digging through multiple case studies, your correspondent has found numerous real-life examples where dating apps have done more harm than good. As said before, it is completely up to the reader how you interpret this article, but when it comes to meeting strangers online, it is better to be safe than sorry. Unfortunately, apps like Tinder, Bumble, and Hinge are just not there yet when it comes to protecting users' physical safety. Not in the slightest. We've all seen the news headlines and heard about the spiked increase in rape and domestic violence cases in association to dating apps. Please heed this warning and think about your physical safety before choosing to commit to a dating app.
CONCERN #2: BREACHES OF PRIVACY
By now, it has probably become exhausting listening to countless security lectures about the numerous ways in which big-tech companies can abuse your data. We have all heard these lectures from the news, government officials, our parents, etc. but at the end of the day, all of these parties are right to worry. Bottom Line: Dating app giants like Tinder, Bumble, and Hinge are huge abusers of user privacy, and they are virtually never apologetic. While some of your data is helpful in guiding the app's matching algorithms to pair a user with profiles, a lot of it actually is not. Before giving away your information willy-nilly, maybe ask yourself:
Does this stuff really matter for finding romance?
Social demographics are shifting, and most of the population would basically answer, yes it is important that my S/O shares the same political party as I do, or that we both belong to the same religion, etc. However, according to ourrelationship.com (a certified couple's therapy site), there is no research indicating that couples with differing political or religious ideologies will break up more than a couple with similar views. It is merely a matter of loving psychology and compatibility rather than your "sameness" that binds people together. If it is the user's preference to look for a companion who is more similar to them and their interests, that's totally fine! Dating apps certainly narrow the pool of choices and help you focus on what you are specifically seeking. But otherwise, we have to question why this type of data is being collected about users if it is not always helpful for romantic connection.
CONCERN #3: YOU ARE WORTH MUCH MORE THAN A COMPUTER
Nobody likes to think about the fact that Artificial Intelligence is dictating your love life, but that's basically the truth with dating apps. A computer is telling you what to do. Who you should like, who you shouldn't like, and who is your "level of desirability" to go out with. If you are wondering what we mean by this, we will tell you: Each user is assigned a score of desirability based on how much of a "catch" they are (according to whoever designed the algorithm). For example: Tinder's "ELO" matching algorithm is entirely centered on the idea of physical attraction and personal appearance rather than any other defining qualities of a person. This makes sense when you think about how small a user's bio is vs. how many "attractive" photos they are required to upload.
To the computer, all that matters is your looks, and according to their judgement, you receive a score of desirability that matches you to the appropriate level of users with similar appearance ratings. If this doesn't bother you, that's okay. When searching for a potential partner, an attractive appearance is the first thing most people notice or go after. However, the principle of this system is what is unacceptable. Not only is a user being told to stay within their lane, but they are also told they are unworthy to reach for a higher "tier". So to sum it up, you are letting a dumb computer tell you that you are not good enough. When the computer is marking you a 6 out of 10, you start thinking of yourself as a 6 out of 10.
Bottom Line: You should always feel worthy enough to approach anybody; no number scale system should dictate who get's to fall in love with who or who you get to go out on a date with. You should be able to be with whoever you want! These dating apps may advertise that they are creating unique connections, but really they may be blocking you from the real connections you want with someone outside of your focus-group. If a computer debilitating your self-worth is not enough of a reason to delete, think about how you may be missing out on the love of your life because of their stupid decisions. delete. delete. delete.

DISCLAIMER: If we still haven't convinced you to steer clear of dating apps, that's okay. We acknowledge that this article was a very long and tiraded rant, but at the end of the day, it lives up to Silicon's mission to keeping users protected and more knowledgeable about their data privacy. Overall, be safe and have fun falling in love! (or not, it's up to you).
Comments